AI Document Automation ThatMakes Work More Meaningful
Reduce operational costs. Save valuable time. Prevent fraud.
Trusted by 1000+ brands worldwide

<img decoding=”async” src=”https://www.klippa.com/wp-content/uploads/2024/02/Banijay-grey-logo.png” alt=””/> 
<img decoding=”async” src=”https://www.klippa.com/wp-content/uploads/2024/02/Online-Payment-Platform-grey-logo.png” alt=””/> 
<img decoding=”async” src=”https://www.klippa.com/wp-content/uploads/2024/02/DZBank-grey-logo.png” alt=””/> 
<img decoding=”async” src=”https://www.klippa.com/wp-content/uploads/2024/02/Nivea-grey-logo.png” alt=””/> 
<img decoding=”async” src=”https://www.klippa.com/wp-content/uploads/2024/02/Krombacher-grey-logo.png” alt=””/> 
<img decoding=”async” src=”https://www.klippa.com/wp-content/uploads/2024/02/Car-Offer-grey-logo.png” alt=””/> 
<img decoding=”async” src=”https://www.klippa.com/wp-content/uploads/2024/02/Car-Offer-grey-logo.png” alt=””/>
Leave Manual Document Processing Behind, Become A Frontrunner In Automation
Reduce turnaround time by 90%
Drastically reduce turnaround times by processing documents in 5 seconds, not minutes.
Maximize your workforce effiency
Empower your workforce to achieve more in less time, by automating repetitive tasks.
Save up to 80% on operational costs
Eliminate data entry work and reduce 80% of your administrative costs with automation.
Detect fraud and ensure compliance
Klippa Products
The Leader In Automated Document Processing
Empower frontline workers, reduce hiring needs, keep employees happy and innovate customer experiences. Leverage Klippa’s AI-powered document processing solutions.
Spend Management Solutions
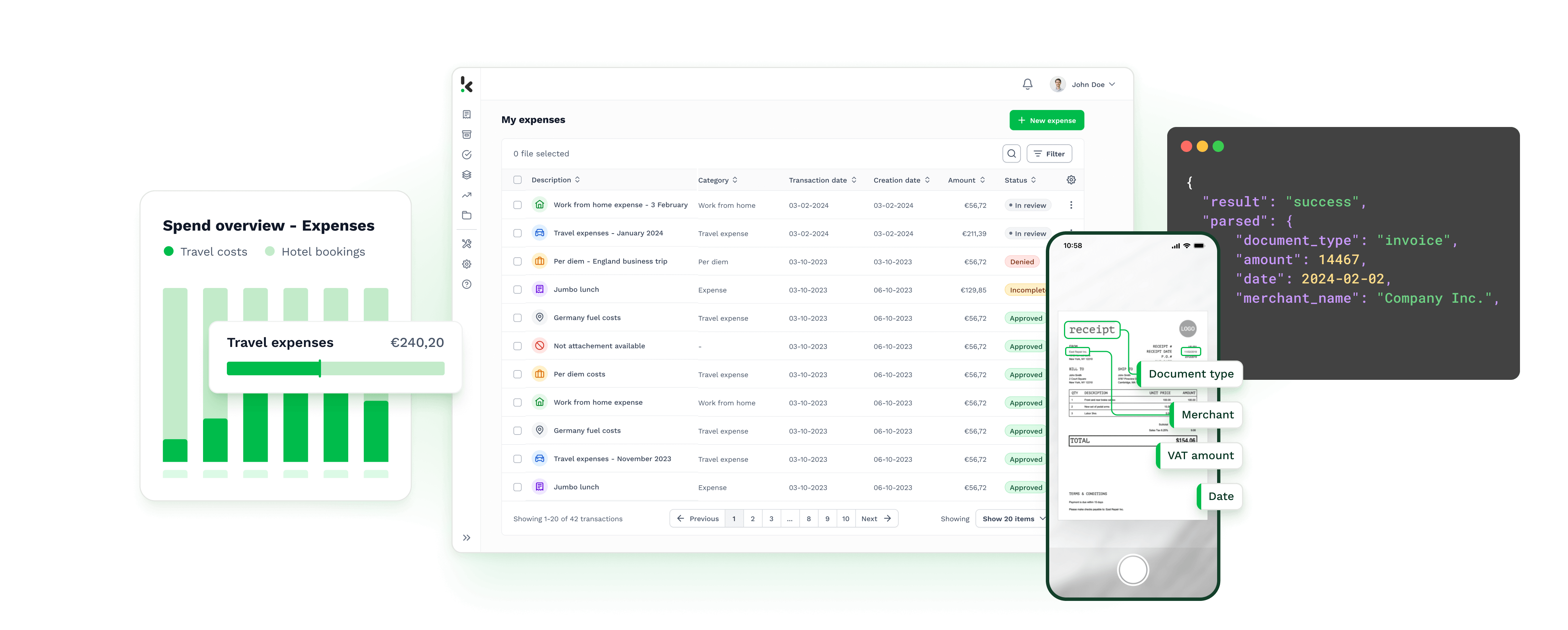
SpendControl provides care free spend management for every financial leader. Control your organizations spend and optimize financial operations, with modules for invoice processing, expense reimbursements and business expense cards.
Intelligent Document Processing
Klippa DocHorizon helps organizations automate document workflows. Turn documents into structured data within seconds. Scan, read, sort, extract, anonymize, convert and verify documents at scale via our interface, APIs or SDK.
What Clients Say About Us
1000+ Brands Automate Workflows With Klippa
Klippa allows us to digitally register, approve, and process expenses and invoices in one user-friendly cloud environment.
We never have to worry about long processing times. The global coverage for identity documents has also been a great advantage.
Klippa’s OCR is fast, accurate, and also easy to implement. The contact with Klippa was always easy, convenient, and nice.
Maximize The Efficiency Of Your Business Processes & Teams
Our cutting-edge AI-powered document automation revolutionizes how companies digitize their data, optimize their workflows, verify document authenticity and more.
How Alasco Automated Invoice Processing In Their Real Estate Software
With Klippa’s OCR, Alasco was able to extract invoice data directly into its own real-estate software.
Your Data Security Guaranteed
At Klippa, your data is treated with utmost care. We comply with global data protection and international privacy regulations.
Get Started Now!
Let Klippa’s experts show you how our smart Document Processing solutions can be integrated into your existing processes.
Discover Our Insightful Blogs
Stay informed with our insightful blogs on intelligent document processing, OCR, invoice processing, and more.