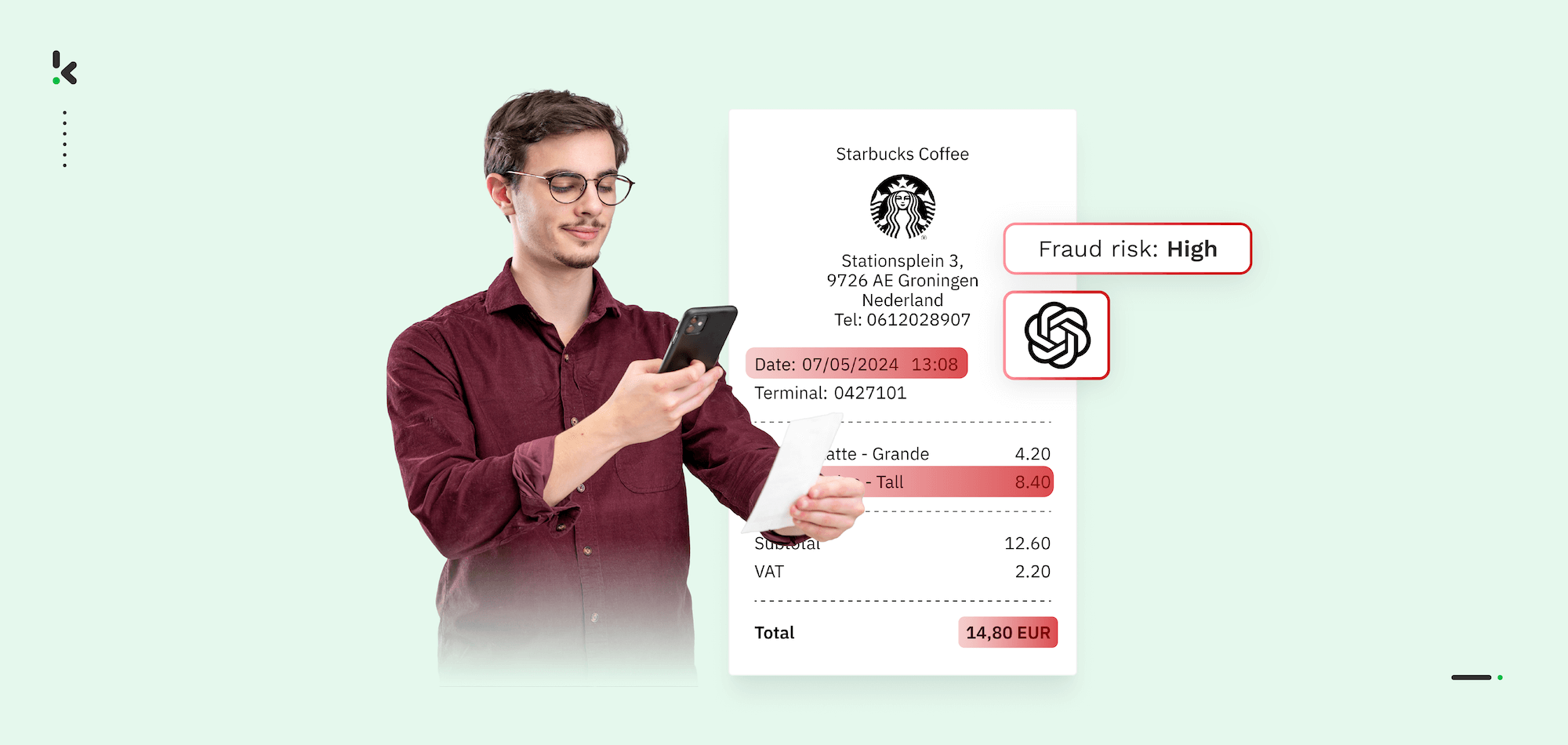

Counterfeit receipts have quietly become one of the biggest threats to businesses that issue refunds, process expenses, offer loyalty rewards, or handle warranty claims. On some platforms, the share of AI-generated fraudulent documents rose from none to 14% within a year.
On the surface, these fakes can look completely authentic. The logo is there, prices look reasonable, and the formatting matches. But hidden inside could be altered totals, changed dates, or entirely fabricated transactions.
The impact? Direct financial loss, operational strain, compliance risks, and potential reputation loss. And thanks to editing tools freely available online (plus specialist fake receipt generators), even non-technical fraudsters can make convincing fakes in minutes.
In this guide, you’ll learn what receipt fraud looks like, how fake receipts are created, and how you can point out tampering in seconds.
Key Takeaways
- Fraudsters can create convincing fake receipts with minimal effort using widely available templates, editing tools, and AI generators.
- Manual inspection can catch obvious cases, but subtle manipulations often escape visual review.
- AI-powered layered detection checks multiple factors like metadata, image composition, duplicate patterns, and external data sources to catch more fraud.
- Integrating prevention policies with technology provides both scale and reliability.
What is a Fake Receipt?
A fake receipt is a falsified proof of purchase intended to misrepresent a transaction. For example, a photographed printout is uploaded as an image file. Fraudsters use them to gain financial benefits, goods, services, or loyalty rewards they are not entitled to.
Common scenarios:
- Corporate expense fraud: Employees submit fabricated taxi, restaurant, or hotel receipts to claim reimbursements for trips or meals never taken.
- Retail refund scams: Customers create receipts for items they never purchased, receiving money back or replacement products.
- Vendor overbilling: Contractors inflate orders or double-charge by attaching duplicate receipts for materials.
- Loyalty points exploitation: Loyalty fraud occurs when a shopper uploads the same legitimate receipt to claim rewards across several accounts.
Forms of fake receipts:
- Fully fabricated: Designed from scratch using templates, receipt generator websites, or graphic design software like Photoshop. They mimic the style of a genuine merchant’s receipt but contain false details.
- Altered authentic receipts: Real receipts that are modified with changed line item prices, altered dates, and replaced merchant names.
- Duplicated authentic receipts: Genuine receipts reused multiple times for separate claims.
These fraud types all share a core tactic: they bypass trust-based assumptions around receipts by presenting a document that looks legitimate at first glance, banking on the fact that most are processed without deep verification.
How Fake Receipts Are Created
Just like fake invoices, fake receipts are crafted deliberately to avoid triggering suspicion. Fraudsters adapt proven document manipulation techniques to fit the flexible, low-regulation world of consumer transaction records.
Receipt cloning
The fraudster starts with a real merchant receipt. They copy everything about it: layout, font style, spacing, item descriptions, and logo placement. The only changes are to key transaction details, such as the date, total, or payment method. Because the structure matches a real receipt exactly, these fakes can pass basic visual checks easily.
Example: A taxi receipt from February is copied, the date altered to March in Photoshop, and the fare increased to cover an inflated reimbursement claim.
Fabricated receipts
These are built entirely from scratch using online generator tools (think Chat GPT) or pre-formatted templates. While fabrication can lead to formatting errors for the trained eye, many businesses lack baseline templates for comparison. This allows obviously false receipts to slip through despite inconsistencies.
Example: An electronics store refund request features a crisp, newly printed receipt. Cross-checking with the chain’s standard POS output shows a mismatched font and a missing merchant ID, revealing it as a generated fake.
Social manipulation for policy exploitation
Beyond the receipt itself, fraudsters benefit from refund or expense policies. They may submit fakes in large batches, hoping most pass without review, or pressure staff with urgency (“the refund must be processed today”).
Price inflation and selective editing
Instead of replacing the entire receipt, some target specific numeric fields (high-value items or total amounts) are edited using editing tools to change amounts. This is particularly effective in loyalty receipt scanning programs or internal expense systems, where matching an item description is enough to qualify for rewards or reimbursement.
Duplicates
Once a receipt has successfully passed verification for a claim, it is often reused. The same document is submitted again, perhaps months later, under a different account, or across multiple platforms.
Why this matters: Each document fraud technique has its own risk profile. Cloning and subtle alterations slip past human reviewers relying on visual comparison. Fabrication and duplication exploit weaknesses in policy and system tracking. The result is the same: the receipt appears valid, the fraud goes undetected, and the business loses money.
How to Spot Fake Receipts: The Red Flags
Before we get into advanced detection methods, it’s worth training your team to recognise the signs that should make them pause during a review. Receipt fraud often leaves recurring “fingerprints” (anomalies in the layout, data, or context) that don’t align with how genuine documents are produced.
Here are the most common and impactful red flags we see when analysing fraudulent receipts, explained with examples.
Unexpected or Unfamiliar Receipts
If your team doesn’t recognise the merchant, the claimed purchase, or the type of items, treat that as a warning. Expense fraud often involves adding charges from unfamiliar vendors, especially in industries where staff travel or purchase from a broad range of merchants.
Merchant Details That Don’t Match
Legitimate receipts include the accurate merchant name, address, and contact information. Fraudsters often use partial details or make subtle changes to pass them off as real. Sometimes the wrong logo is inserted, or outdated addresses are used.
Example: A hardware store refund request features the brand’s old address from a location closed three years ago. A simple lookup on the Chamber of Commerce database confirms the store relocated, and the receipt format should have changed accordingly.
Formatting and Font Inconsistencies
Genuine POS systems output consistent font styles and sizes for all printed fields. On fake receipts, altered values often stand out: sharper, darker, or slightly larger than surrounding text because they’ve been retyped or pasted in.
Example: A hotel receipt total is in a heavier bold font compared to the rest of the items. Image forensic analysis later confirms the number was pasted from another source.
Arithmetic Errors
Most legitimate receipts add subtotals, VAT (or local equivalent), and totals correctly. When fraudsters change line item prices, they sometimes forget to adjust the math. Odd or rounded totals that don’t match expected calculations can be a giveaway.
Suspicious Dates and Times
Dates outside trading hours, service times during holidays, or purchase times that clash with known operational schedules should trigger further review.
Missing or Generic Receipt Identifiers
Receipts normally carry unique transactional details such as a receipt number, transaction code, or merchant terminal ID. Fake receipts may omit these entirely or use generic placeholders.
Duplicate Receipts Across Submissions
If the same receipt appears more than once in your system, even with minor changes, it should be flagged for investigation. Small scams often rely on resubmitting prior documents where review processes assume previous approval equals validity.
Non-standard Payment Details
Card payments without masked digits, cash entries with unusually precise decimal figures, or mismatched payment method descriptions can signal fabrication.
Training reviewers to spot these signs is the first layer of defence. But where manual vigilance ends, technology can take over, especially for catching subtler anomalies and high-volume fraud.
Test yourself by guessing which receipt is fake in our video:
How to Protect Your Company from Fake Receipts
Knowing the red flags is only step one. Protection comes from building a system of checks and controls that combine human judgment with automation. This ensures your team can process genuine receipts quickly while stopping fraudulent ones before they do harm.
1. Move Beyond Purely Manual Review – Fake receipts are designed to bypass visual checks. An edited PDF with perfect branding and matching spacing can fool even the most experienced reviewer.
2. Create a Library of Genuine Receipts – For key merchants or frequent vendors in your network, store examples of real receipts as issued by their POS systems. Compare suspicious receipts against this baseline.
3. Implement Duplicate Detection – Track receipt details across submissions. Generate a digital fingerprint (hash) for each receipt containing its total, date, and transaction number. Any match triggers a duplicate alert.
4. Match Receipt Details with Transaction Data – Integrate receipt review with payment system logs, POS data, or ERP purchase orders. If a receipt claims a date and time with no matching transaction in your records, it’s fraudulent.
5. Require Original Digital Source Files – Where possible, receipts should be obtained directly from a merchant’s POS system or via official email confirmation, not through screenshots or scanned printouts.
6. Combine Human and AI Review – Humans excel at contextual judgement, deciding if an expense is reasonable given circumstances. AI excels at high-volume anomaly detection, pattern recognition, and pixel-level image forensics. Layering these strengths captures both obvious and subtle fraud.
Pro tip: Receipt fraud prevention isn’t static. Regularly review your detection policies alongside new fraud trends. What slipped through last quarter shouldn’t slip through again.
How to Identify Fake Receipts with AI
Manual checks stop the obvious fraud. But more complicated scams (especially those created with high-grade templates, generative AI, or professional editing tools) are designed to slip past human reviewers.
This is where layered AI-powered fraud detection comes in. Instead of relying on a single test, Klippa DocHorizon applies a series of independent checks to every receipt. Each focuses on a different manipulation technique, so if one doesn’t catch it, another will.
Here’s how these layers work for catching fake receipts.
Metadata & EXIF Analysis
Every digital file carries hidden metadata: time and date of creation, last modification date, the software used for editing, and sometimes even GPS location for photographs.
Fraudsters rarely remove every trace. A receipt claiming to be from 10 February 2025 might show metadata revealing it was created two weeks later in Adobe Photoshop. Or an image taken on a smartphone could contain GPS coordinates that don’t match the store location.
Klippa DocHorizon systematically extracts and checks this metadata against the visible receipt details, flagging mismatches for review.
Copy-Move Detection
Copy-move detection identifies duplicated pixel clusters within an image. On receipts, this often reveals repeated use of a single digit or logo element, copy‑pasted into multiple locations.
For instance, a loyalty program fraud may involve copying the number “3” to create higher totals, €13.20 becoming €33.20, while leaving the rest of the formatting intact. To a human, this might look fine. To Klippa DocHorizon, identical pixel patterns are mapped instantly, exposing the manipulation.
Image Splicing Detection
Splicing occurs when content from an external source (e.g., another receipt, a logo file, or a “Paid” stamp) is inserted into the image.
Klippa’s AI compresses the file to reveal subtle boundary markers around inserted elements. These edges, invisible to the naked eye, are precisely what the model is trained to recognise.
Example: A refund request contains the store’s correct logo, but image splicing detection reveals it was pasted from a marketing flyer, not generated by the store’s POS.
Duplicate Detection (Hash Checks)
Klippa creates a hash for each receipt based on key fields like total amount, purchase date, and receipt number. Any new submission with a matching hash is flagged as a duplicate, even if the image resolution or file type is different.
Mathematical Validation
Receipts include line items, subtotals, taxes, and totals. Klippa recalculates these values, comparing its results to what appears on the document.
Example: A corporate travel receipt lists four line items adding to €236.00, with 21% VAT. The stated VAT is €25.00 instead of the correct €49.56.
Font Anomaly Detection
When fraudsters alter receipts, they often insert numbers or text using fonts that don’t exactly match the originals. Even small differences in font weight, spacing, or typeface are detectable.
Klippa analyses font consistency across the receipt, flagging any mismatches in sections where all text should be the same.
Chamber of Commerce Verification
Receipt fraud often involves invented businesses or inactive merchant names. Klippa cross-checks the merchant’s details against official business registries, confirming:
- The business exists
- The address matches registration records
- The business status is active (not bankrupt or deregistered)
A mismatch means the receipt is suspicious by default, triggering further review.
AI Price Validation
For receipts detailing products or services, Klippa’s fraud detection AI agents automatically search the merchant’s current catalogue or public listings. Prices exceeding the official rate are flagged as possible inflation.
Example: A hardware store receipt lists an electric drill at €215.00. Klippa’s AI finds the same model on the store’s official website for €165.00, indicating overbilling or fabrication.
Why a Layered Approach Works Best
Fraudsters usually change one element (e.g., a total, a merchant name, a date) and hope a manual check won’t spot it. Layered detection removes that advantage by running multiple, independent checks on every receipt:
- If it passes visual inspection, metadata may still reveal tampering
- If metadata looks clean, duplicate detection or price validation can still catch it
- AI scans every receipt at scale, so no document slips through due to human factor
- Built‑in duplicate matching stops repeat claims and loyalty abuse
- Real‑time processing means genuine receipts move unhindered while suspicious ones are flagged instantly
In short: Fraudsters can hide one mistake, but they can’t hide them all, and Klippa DocHorizon checks them all in seconds. Watch our webinar “How to Detect Document Fraud & Image Tampering” to see this in action:
Klippa DocHorizon: The Best Receipt Fraud Detection Software
Fraudsters are moving from obvious, easily spotted alterations to subtle, AI-polished manipulations that blend seamlessly into legitimate workflows. The only reliable defence is a system that knows how to check what humans can’t see, and does it in real time.
Klippa DocHorizon is a fully AI-powered document processing platform designed to automatically verify authenticity, detect manipulation, and reduce the risk of receipt fraud, whether you process hundreds or thousands of receipts each month.
Klippa DocHorizon offers a fully equipped Intelligent Document Processing platform that seamlessly integrates data extraction, image forensics, and compliance automation. With our solution, you can:
- Extract and validate data with 99% accuracy using AI-powered OCR
- Detect forged or altered receipts instantly using advanced image forensics (copy-move & splicing analysis)
- Perform metadata and EXIF analysis to uncover hidden creation and editing traces
- Run duplicate detection with hash-matching to stop the same receipt from being claimed multiple times
- Validate totals and VAT calculations with mathematical checks
- Spot hidden formatting changes with font anomaly detection
- Cross-check business data with official Chamber of Commerce records to confirm authenticity
- Integrate effortlessly via API, SDK, SFTP, or 200+ prebuilt system connections
- Ensure compliance and data security with ISO 27001-certified servers and GDPR-compliant data handling
Want to see how it works? Book a demo or contact us to let our team walk you through real-world fraud detection examples tailored to your industry.
FAQ
Receipt fraud occurs when someone submits a forged, altered, or duplicated receipt to misrepresent a transaction for personal gain. This could mean claiming reimbursement for expenses never incurred, obtaining refunds for products not purchased, inflating purchase prices, or earning loyalty points multiple times for the same purchase.
Receipt fraud detection refers to the processes and tools used to identify and prevent fraudulent receipts from being accepted or processed. These methods aim to spot irregularities such as forged details, unauthorized changes, or suspicious patterns.
Look for red flags such as:
– Merchant details that don’t match official records
– Inconsistent or mismatched fonts and formatting
– Arithmetic errors between line items, subtotals, and totals
– Dates or times outside trading hours
– Missing unique identifiers like receipt numbers
– Duplicates of receipts already processed
For subtle cases, AI-powered detection tools like Klippa DocHorizon combine visual checks, metadata analysis, duplicate detection, and cross-verification to spot fraud that the human eye might miss.
Receipt cloning: Copying a real receipt and changing key details.
Fabricated receipts: Creating a receipt entirely from scratch using templates.
Price inflation: Increasing line item values without adjusting tax or totals properly.
Duplicate submissions: Reusing the same receipt for multiple claims.
Refund scams: Fabricating merchant receipts to get money back or exchange goods.
Yes. Manually, reviewers can catch formatting errors or obvious fakes. But sophisticated scams can pass visual checks. AI detects anomalies that humans can’t see, from hidden metadata mismatches to pixel-level image alterations, duplicate hashes, and price inconsistencies in real time.
Retailers, HR departments, finance teams, insurance companies, warranty services, and auditors all use receipt fraud detection procedures.
Optical Character Recognition (OCR) tools, machine learning models for pattern recognition, ERP systems with fraud modules, and secure transaction databases are commonly used.
Automation speeds up detection and scans large volumes of receipts efficiently, but human expertise is often necessary for borderline or complex cases.